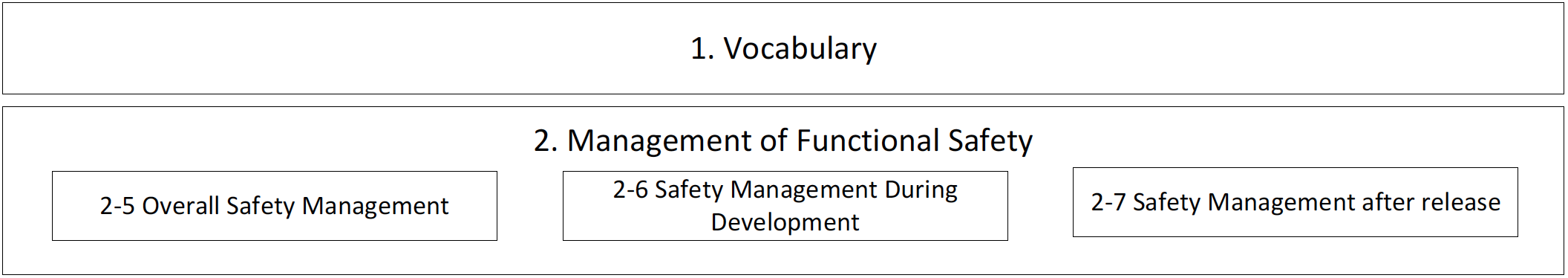
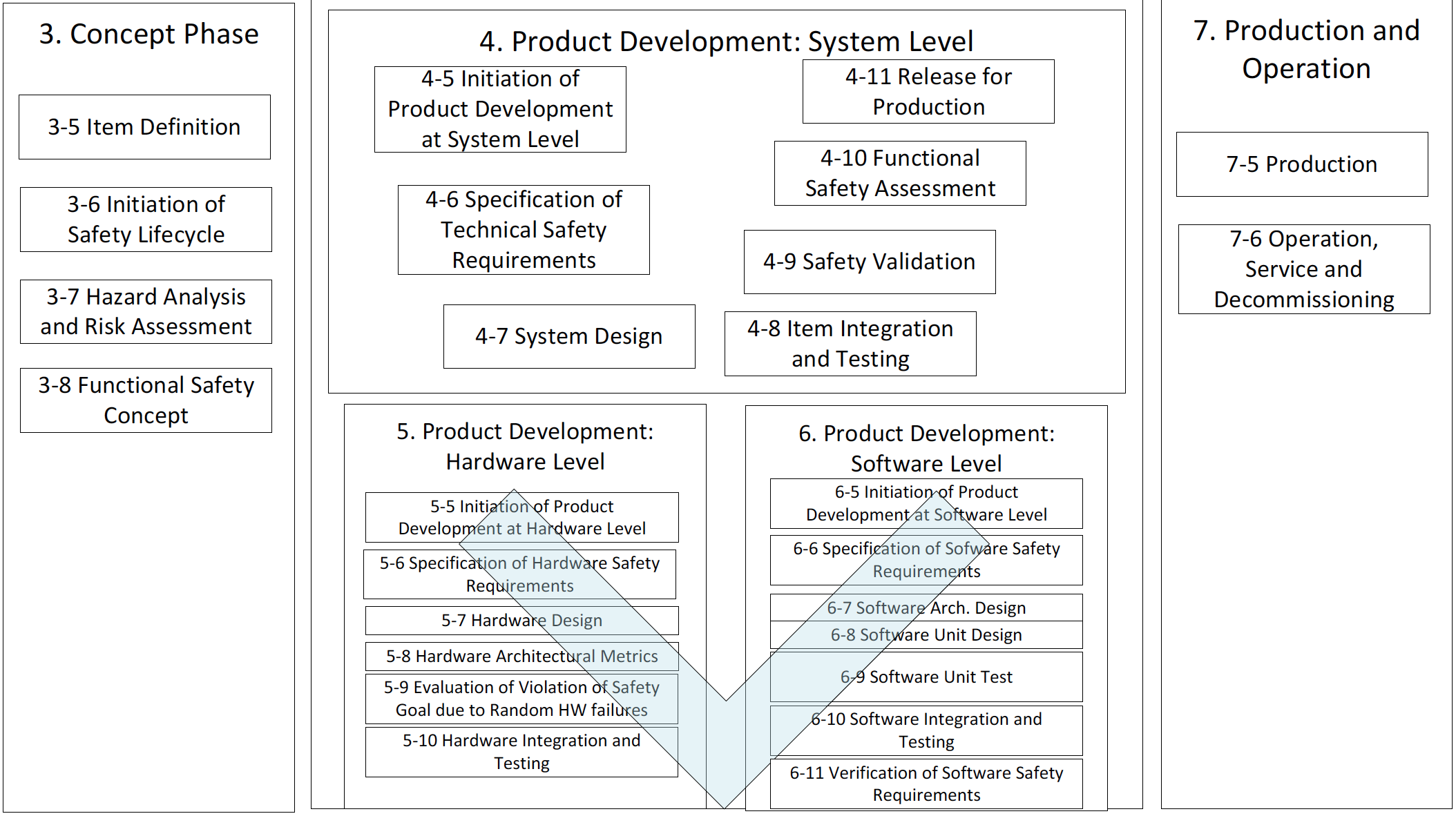
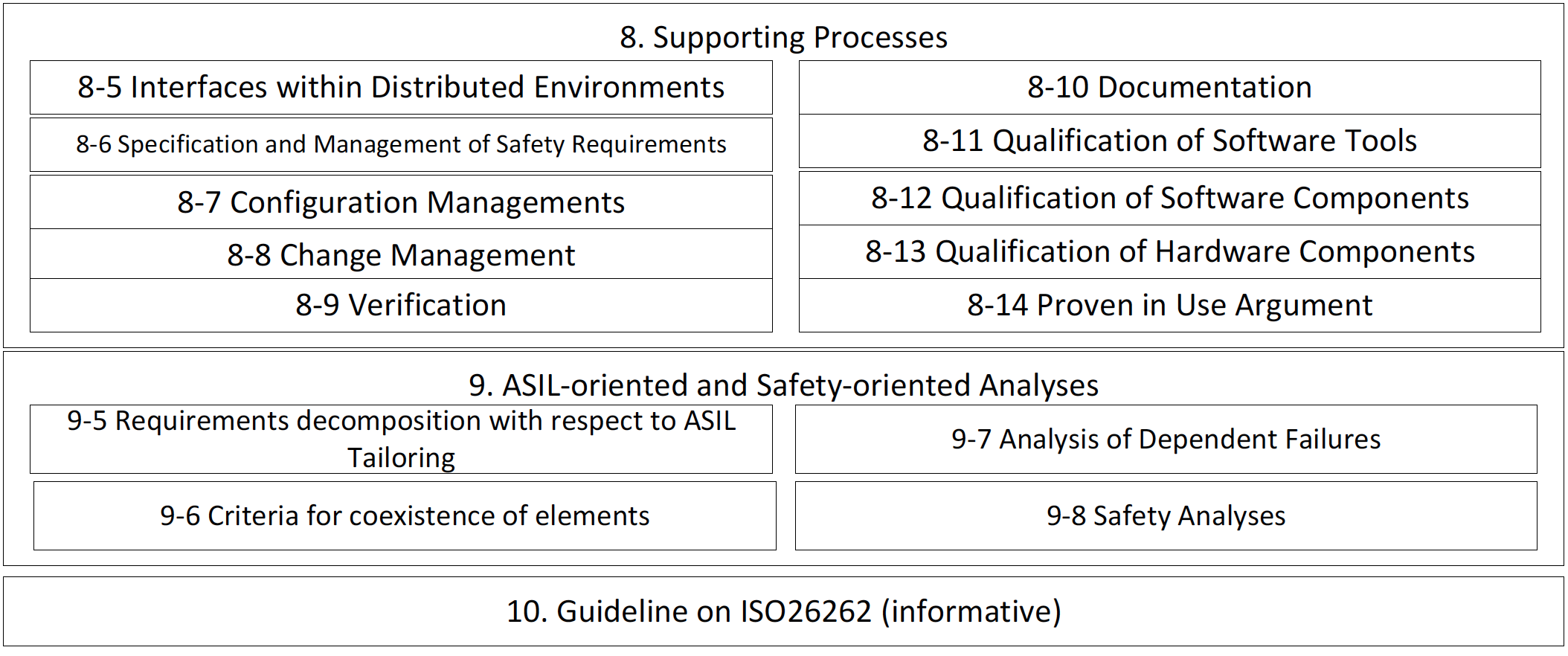
Trends in automotive design are moving towards ever-increasing use of software, the integration of software components at various levels of safety, and regulatory compliance with ISO 26262.
Get the background on ISO 26262 processes and what parts of the standard apply to COTS software components.
Learn essential characteristics of COTS software that you can use in road vehicle design for compliance with ISO 26262.
Discover the documentation and evidence required to assist you in achieving ISO 26262 compliance for current and future projects.
See an example of what constitutes a reusable software component from our partner company RTI.